这周五开始做了一个华为模拟器的混合实验,我想分享一下。
以下是拓扑图:
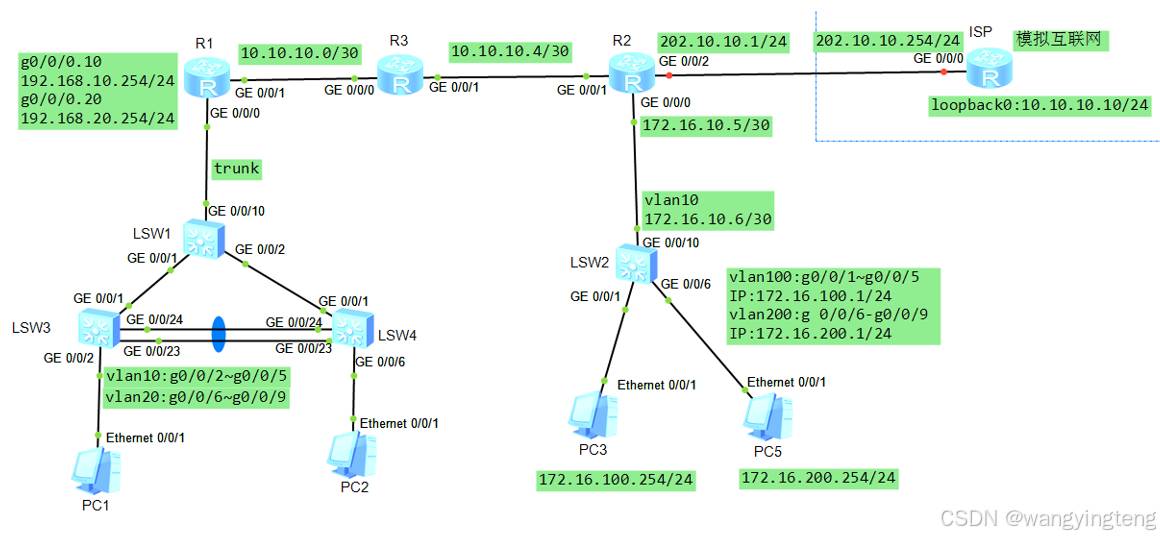
在 eNSP 模拟器中,按照样图绘制网络拓扑结构图,不需要添加注释(绿色背景部分)。其中路由器使用 Router 设备,交换机使用 S5700 设备,终端使用PC 设备。
(1)根据下表要求在交换机中完成设备名称、vlan及相应VLAN接口IP地址配置。
设备名称 VLAN编号 端口 IP地址
LSW1 10、20
LSW2 10 Ge 0/0/10 172.16.10.6/30
100 Ge 0/0/1~Ge 0/0/5 172.16.100.1/24
200 Ge 0/0/6~Ge 0/0/9 172.16.200.1/24
LSW3 10 Ge 0/0/2~Ge 0/0/5
20 Ge 0/0/6~Ge 0/0/9
LSW4 10 Ge 0/0/2~Ge 0/0/5
20 Ge 0/0/6~Ge 0/0/9
user-int vty 0 4 //进入vty用户界面视图
Protocol inbound telnet //配置vty用户支持telnet协议 pro in t
authentication-mode password //设置验证方式为密码验证 auth pa
set authentication password cipher huawei //设置登录密码为huawei
Set auth pa ci huawei
user privilege level 15 //设置登录用户默认级别15
公网地址池:202.10.10.1~202.10.10.10
题目中提到了ospf、stp、动态路由、静态路由、端口安全、telnet、nat
我们可以从下向上进行实施,通常是这样进行配置的。
对于一些特殊部分,我们可以通过标注文字来备注
可以将他们分成几块,分别按步骤来配置。
[sw1]vlan batch 10 20
[sw2]vlan batch 10 20
[sw3]vlan batch 10 20
[r1]vlan batch 10 20
[sw3]interface Eth-Trunk 1
[sw3-Eth-Trunk1]trunkport GigabitEthernet 0/0/23 to 0/0/24
[sw3-Eth-Trunk1]port link-type trunk
[sw3-Eth-Trunk1]port trunk allow-pass vlan all
[sw4]interface Eth-Trunk 1
[sw4-Eth-Trunk1]trunkport GigabitEthernet 0/0/23 to 0/0/24
[sw4-Eth-Trunk1]port link-type trunk
[sw4-Eth-Trunk1]port trunk allow-pass vlan all
[sw3]stp root primary
[sw2]stp root secondary
[sw3-GigabitEthernet0/0/1]port link-type trunk
[sw3-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[sw2-GigabitEthernet0/0/1]port link-type trunk
[sw2-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[sw1]port-group 1
[sw1-port-group-1]group-member g0/0/1 g0/0/2 g0/0/10
[sw1-port-group-1]port link-type trunk
[sw1-GigabitEthernet0/0/1]port link-type trunk
[sw1-GigabitEthernet0/0/2]port link-type trunk
[sw1-GigabitEthernet0/0/10]port link-type trunk
[sw3]port-group 1
[sw3-port-group-1]group-member g0/0/2 to g0/0/5
[sw3-port-group-1]port link-type access
[sw3-GigabitEthernet0/0/2]port link-type access
[sw3-GigabitEthernet0/0/3]port link-type access
[sw3-GigabitEthernet0/0/4]port link-type access
[sw3-GigabitEthernet0/0/5]port link-type access
[sw3-port-group-1]port default vlan 10
[sw3-GigabitEthernet0/0/2]port default vlan 10
[sw3-GigabitEthernet0/0/3]port default vlan 10
[sw3-GigabitEthernet0/0/4]port default vlan 10
[sw3-GigabitEthernet0/0/5]port default vlan 10
[sw3]port-group 2
[sw3-port-group-2]group-member g0/0/6 to g0/0/9
[sw3-port-group-2]port link-type access
[sw3-GigabitEthernet0/0/6]port link-type access
[sw3-GigabitEthernet0/0/7]port link-type access
[sw3-GigabitEthernet0/0/8]port link-type access
[sw3-GigabitEthernet0/0/9]port link-type access
[sw3-port-group-2]port default vlan 20
[sw3-GigabitEthernet0/0/6]port default vlan 20
[sw3-GigabitEthernet0/0/7]port default vlan 20
[sw3-GigabitEthernet0/0/8]port default vlan 20
[sw3-GigabitEthernet0/0/9]port default vlan 20
[sw2]port-group 3
[sw2-port-group-3]group-member g0/0/2 to g0/0/5
[sw2-port-group-3]port link-type access
[sw2-GigabitEthernet0/0/2]port link-type access
[sw2-GigabitEthernet0/0/3]port link-type access
[sw2-GigabitEthernet0/0/4]port link-type access
[sw2-GigabitEthernet0/0/5]port link-type access
[sw2-port-group-3]port default vlan 10
[sw2-GigabitEthernet0/0/2]port default vlan 10
[sw2-GigabitEthernet0/0/3]port default vlan 10
[sw2-GigabitEthernet0/0/4]port default vlan 10
[sw2-GigabitEthernet0/0/5]port default vlan 10
[sw2]port-group 2
[sw2-port-group-2]group-member g0/0/6 to g0/0/9
[sw2-port-group-2]port link-type access
[sw2-GigabitEthernet0/0/6]port link-type access
[sw2-GigabitEthernet0/0/7]port link-type access
[sw2-GigabitEthernet0/0/8]port link-type access
[sw2-GigabitEthernet0/0/9]port link-type access
[sw2-port-group-2]port default vlan 20
[sw2-GigabitEthernet0/0/6]port default vlan 20
[sw2-GigabitEthernet0/0/7]port default vlan 20
[sw2-GigabitEthernet0/0/8]port default vlan 20
[sw2-GigabitEthernet0/0/9]port default vlan 20
[r1]dhcp enable
[r1]int g0/0/0.1
[r1-GigabitEthernet0/0/0.1]ip add 192.168.10.254 24
[r1-GigabitEthernet0/0/0.1]dot1q termination vid 10
[r1-GigabitEthernet0/0/0.1]arp broadcast enable
[r1-GigabitEthernet0/0/0.1]dhcp select interface
[r1-GigabitEthernet0/0/0.1]dhcp select interface
[r1]int g0/0/0.2
[r1-GigabitEthernet0/0/0.2]ip add 192.168.20.254 24
[r1-GigabitEthernet0/0/0.2]dot1q termination vid 20
[r1-GigabitEthernet0/0/0.2]arp broadcast enable
[r1-GigabitEthernet0/0/0.2]dhcp select interface
[r1-GigabitEthernet0/0/0.2]dhcp select interface
[r1-GigabitEthernet0/0/1]ip add 10.10.10.1 24
[r3-GigabitEthernet0/0/0]ip add 10.10.10.2 24
[r3-GigabitEthernet0/0/1]ip add 10.10.10.5 30
[r2-GigabitEthernet0/0/1]ip add 10.10.10.6 30
[r4-GigabitEthernet0/0/0]ip add 202.10.10.254 24
要注意:因为子网掩码为30,所以10.10.10.4网段的可用IP地址仅有10.10.10.5和10.10.10.6
[r2-GigabitEthernet0/0/0]ip add 172.16.10.5 30
[r2-GigabitEthernet0/0/2]ip add 202.10.10.1 24
[sw2]vlan ba 100 200 10
[sw2]port-group 1
[sw2-port-group-1]group-member g0/0/1 to g0/0/5
[sw2-port-group-1]port link-type access
[sw2-GigabitEthernet0/0/1]port link-type access
[sw2-GigabitEthernet0/0/2]port link-type access
[sw2-GigabitEthernet0/0/3]port link-type access
[sw2-GigabitEthernet0/0/4]port link-type access
[sw2-GigabitEthernet0/0/5]port link-type access
[sw2-port-group-1]port default vlan 100
[sw2-GigabitEthernet0/0/1]port default vlan 100
[sw2-GigabitEthernet0/0/2]port default vlan 100
[sw2-GigabitEthernet0/0/3]port default vlan 100
[sw2-GigabitEthernet0/0/4]port default vlan 100
[sw2-GigabitEthernet0/0/5]port default vlan 100
[sw2]port-group 2
[sw2-port-group-2]group-member g0/0/6 to g0/0/9
[sw2-port-group-2]port link-type access
[sw2-GigabitEthernet0/0/6]port link-type access
[sw2-GigabitEthernet0/0/7]port link-type access
[sw2-GigabitEthernet0/0/8]port link-type access
[sw2-GigabitEthernet0/0/9]port link-type access
[sw2-port-group-2]port default vlan 200
[sw2-GigabitEthernet0/0/6]port default vlan 200
[sw2-GigabitEthernet0/0/7]port default vlan 200
[sw2-GigabitEthernet0/0/8]port default vlan 200
[sw2-GigabitEthernet0/0/9]port default vlan 200
[sw2]int g0/0/10
[sw2-GigabitEthernet0/0/10]port link-type access
[sw2-GigabitEthernet0/0/10]port default vlan 10
[sw2]int vlan 100
[sw2-Vlanif100]ip address 172.16.100.1 24
[sw2]int vlan 200
[sw2-Vlanif200]ip add 172.16.200.1 24
[sw2]int vlan 10
[sw2-Vlanif10]ip add 172.16.10.6 30
ospf 1
area 0.0.0.0
network 10.10.10.0 0.0.0.255
network 10.10.10.4 0.0.0.3
network 172.16.10.4 0.0.0.3
network 172.16.100.0 0.0.0.255
network 172.16.200.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
[r1]acl 3000
[r1-acl-adv-3000]rule deny ip source 192.168.0.0 0.0.255.255 destination 172.16.100.0 0.0.0.255
[r1]int g0/0/1
[r1-GigabitEthernet0/0/1]traffic-filter outbound acl 3000
[sw2]int g0/0/1
[sw2-GigabitEthernet0/0/1]port-security enable
[sw2-GigabitEthernet0/0/1]port-security mac-address sticky
[sw2-GigabitEthernet0/0/1]port-security max-mac-num 1
[sw2]mac-address static 5489-9805-182E g0/0/1 vlan 100
[r2]user-interface vty 0 4
[r2-ui-vty0-4]authentication-mode aaa
[r2]aaa
[r2-aaa]local-user zonghe password cipher huawei
[r2-aaa]local-user zonghe privilege level 15
[r2]ip route-static 0.0.0.0 0 202.10.10.254
在这里我们要了解----设置默认路由:因为内网不认识外网,ospf只限于内网,所以想让内网访问外网要借助默认路由,一直到边界路由器,不用配置回来的默认路由,也可以说是只出不进
[r1]ip route-static 0.0.0.0 0 10.10.10.2
[r3]ip route-static 0.0.0.0 0 10.10.10.6
[r2]ip route-static 0.0.0.0 0.0.0.0 202.10.10.254
[sw2]ip route-static 0.0.0.0 0 172.16.10.5
[r2]acl number 2000
[r2-acl-basic-2000]rule 5 permit source 192.168.10.0 0.0.0.255
rule 6 permit source 92.168.20.0 0.0.0.255
rule 7 permit source 10.10.10.0 0.0.0.255
rule 8 permit source 10.10.10.4 0.0.0.3
rule 9 permit source 172.16.10.4 0.0.0.3
rule 10 permit source 172.16.100.0 0.0.0.255
rule 11 permit source 172.16.200.0 0.0.0.255
[r2]nat address-group 1 202.10.10.2 202.10.10.5
[r2-GigabitEthernet0/0/2]nat outbound 2000 address-group 1 no-pat
按照要求将结果粘贴至指定的表格框中,粘贴位错误不得分。
1.绘制网络拓扑结构图
将eNSP模拟器中的网络拓扑截图,粘贴图片至下面。
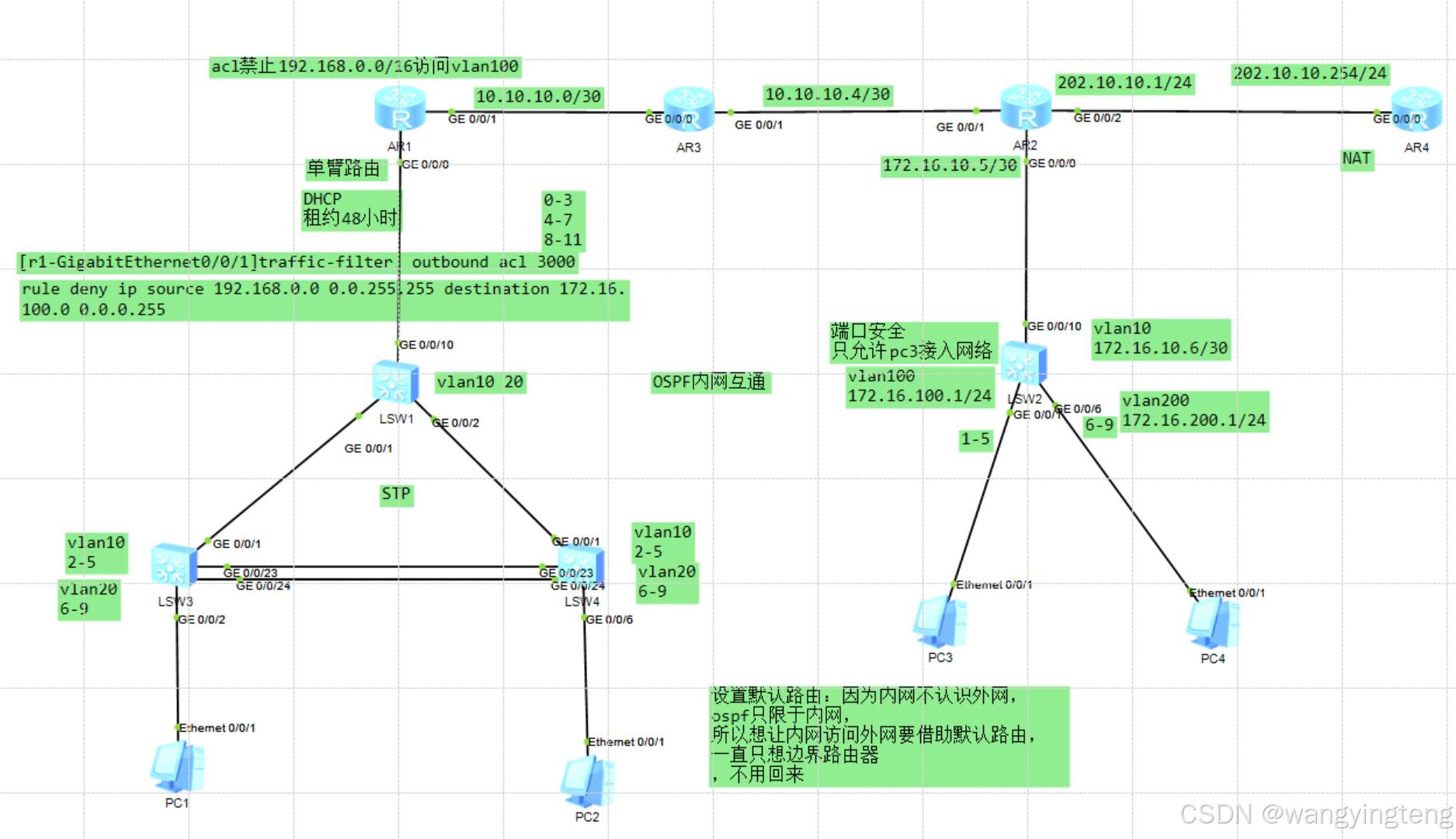
2.网络设备调试
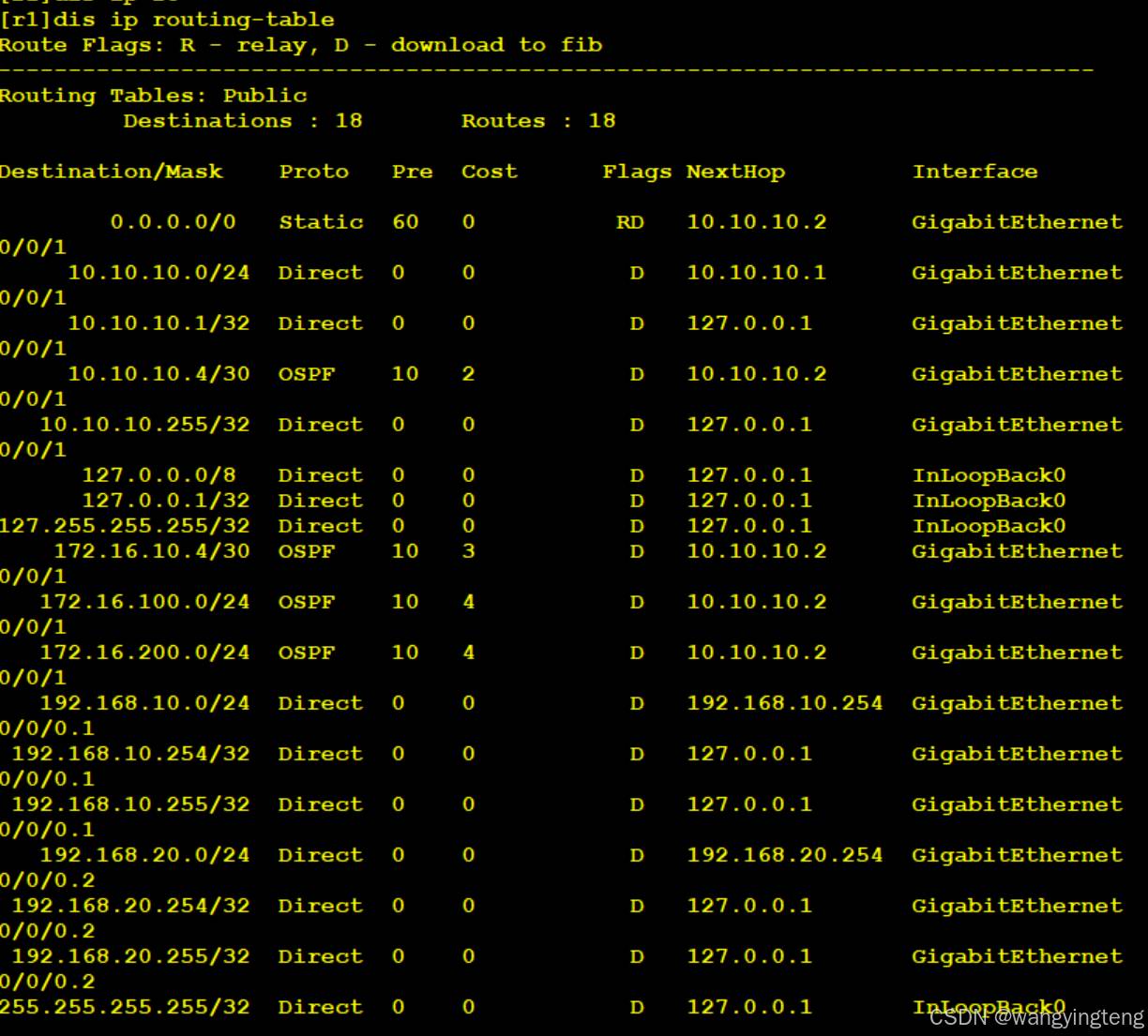
(1)在路由器R1中,执行display ip routing-table命令,并将输出结果以文本形式粘贴至下面。
由于不能将效果复制到这里,所以只能截屏了
(2)在路由器R1中,执行dis current-configuration命令,并将输出结果以文本形式粘贴至下面。
[r1]dis cu
[V200R003C00]
sysname r1
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
undo info-center enable
vlan batch 10 20
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
dhcp enable
acl number 3000
rule 5 deny ip source 192.168.0.0 0.0.255.255 destination 172.16.100.0 0.0.0.25
5
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %
%
K8m.Nt84DZ}e#<0`8bmE3Uw}%
%
local-user admin service-type http
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
interface GigabitEthernet0/0/0.1
dot1q termination vid 10
ip address 192.168.10.254 255.255.255.0
arp broadcast enable
dhcp select interface
dhcp server lease day 2 hour 0 minute 0
interface GigabitEthernet0/0/0.2
dot1q termination vid 20
ip address 192.168.20.254 255.255.255.0
arp broadcast enable
dhcp select interface
dhcp server lease day 2 hour 0 minute 0
interface GigabitEthernet0/0/1
ip address 10.10.10.1 255.255.255.0
traffic-filter outbound acl 3000
interface GigabitEthernet0/0/2
interface NULL0
ospf 1
area 0.0.0.0
network 10.10.10.0 0.0.0.255
network 10.10.10.4 0.0.0.3
network 172.16.10.4 0.0.0.3
network 172.16.100.0 0.0.0.255
network 172.16.200.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
ip route-static 0.0.0.0 0.0.0.0 10.10.10.2
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
(3)在路由器R2中,执行display current-configuration命令,并将输出结果以文本形式粘贴至下面。
[V200R003C00]
sysname r2
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
undo info-center enable
set cpu-usage threshold 80 restore 75
acl number 2000
rule 5 permit source 192.168.10.0 0.0.0.255
rule 6 permit source 92.168.20.0 0.0.0.255
rule 7 permit source 10.10.10.0 0.0.0.255
rule 8 permit source 10.10.10.4 0.0.0.3
rule 9 permit source 172.16.10.4 0.0.0.3
rule 10 permit source 172.16.100.0 0.0.0.255
rule 11 permit source 172.16.200.0 0.0.0.255
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %
%
K8m.Nt84DZ}e#<0`8bmE3Uw}%
%
local-user admin service-type http
local-user zonghe password cipher %
%
}GLD8!(}PMKaTeX parse error: Expected 'EOF', got '&' at position 1: &̲{CMUGu\EG3aI%%$
local-user zonghe privilege level 15
firewall zone Local
priority 15
nat address-group 1 202.10.10.2 202.10.10.5
interface GigabitEthernet0/0/0
ip address 172.16.10.5 255.255.255.252
interface GigabitEthernet0/0/1
ip address 10.10.10.6 255.255.255.252
interface GigabitEthernet0/0/2
ip address 202.10.10.1 255.255.255.0
nat outbound 2000 address-group 1 no-pat
interface NULL0
ospf 1
area 0.0.0.0
network 10.10.10.0 0.0.0.255
network 10.10.10.4 0.0.0.3
network 172.16.10.4 0.0.0.3
network 172.16.100.0 0.0.0.255
network 172.16.200.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
ip route-static 0.0.0.0 0.0.0.0 202.10.10.254
user-interface con 0
authentication-mode password
user-interface vty 0 4
authentication-mode aaa
user-interface vty 16 20
wlan ac
return
(4)在交换机LSW1中,执行display stp brief命令,并将输出结果以文本形式粘贴至下面。

(5)在交换机LSW2中,执行display vlan命令,并将输出结果以文本形式粘贴至下面。

(6)在交换机LSW2中,执行display current configuration命令,并将输出结果以文本形式粘贴至下面。
sysname sw2
undo info-center enable
vlan batch 10 100 200
cluster enable
ntdp enable
ndp enable
drop illegal-mac alarm
diffserv domain default
drop-profile default
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
interface Vlanif1
interface Vlanif10
ip address 172.16.10.6 255.255.255.252
interface Vlanif100
ip address 172.16.100.1 255.255.255.0
interface Vlanif200
ip address 172.16.200.1 255.255.255.0
interface MEth0/0/1
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
port-security enable
port-security mac-address sticky
interface GigabitEthernet0/0/2
port link-type access
port default vlan 100
interface GigabitEthernet0/0/3
port link-type access
port default vlan 100
interface GigabitEthernet0/0/4
port link-type access
port default vlan 100
interface GigabitEthernet0/0/5
port link-type access
port default vlan 100
interface GigabitEthernet0/0/6
port link-type access
port default vlan 200
interface GigabitEthernet0/0/7
port link-type access
port default vlan 200
interface GigabitEthernet0/0/8
port link-type access
port default vlan 200
interface GigabitEthernet0/0/9
port link-type access
port default vlan 200
interface GigabitEthernet0/0/10
port link-type access
port default vlan 10
interface GigabitEthernet0/0/11
interface GigabitEthernet0/0/12
interface GigabitEthernet0/0/13
interface GigabitEthernet0/0/14
interface GigabitEthernet0/0/15
interface GigabitEthernet0/0/16
interface GigabitEthernet0/0/17
interface GigabitEthernet0/0/18
interface GigabitEthernet0/0/19
interface GigabitEthernet0/0/20
interface GigabitEthernet0/0/21
interface GigabitEthernet0/0/22
interface GigabitEthernet0/0/23
interface GigabitEthernet0/0/24
interface NULL0
ospf 1
area 0.0.0.0
network 10.10.10.0 0.0.0.255
network 10.10.10.4 0.0.0.3
network 172.16.10.4 0.0.0.3
network 172.16.100.0 0.0.0.255
network 172.16.200.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
ip route-static 0.0.0.0 0.0.0.0 172.16.10.5
mac-address static 5489-9805-182e GigabitEthernet0/0/1 vlan 100
user-interface con 0
user-interface vty 0 4
port-group 1
group-member GigabitEthernet0/0/1
group-member GigabitEthernet0/0/2
group-member GigabitEthernet0/0/3
group-member GigabitEthernet0/0/4
group-member GigabitEthernet0/0/5
port-group 2
group-member GigabitEthernet0/0/6
group-member GigabitEthernet0/0/7
group-member GigabitEthernet0/0/8
group-member GigabitEthernet0/0/9
return
(7)在交换机LSW3中,执行display current configuration命令,并将输出结果以文本形式粘贴至下面。
sysname sw3
undo info-center enable
vlan batch 10 20
stp instance 0 root primary
cluster enable
ntdp enable
ndp enable
drop illegal-mac alarm
diffserv domain default
drop-profile default
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
interface Vlanif1
interface MEth0/0/1
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
interface GigabitEthernet0/0/2
port link-type access
port default vlan 10
interface GigabitEthernet0/0/3
port link-type access
port default vlan 10
interface GigabitEthernet0/0/4
port link-type access
port default vlan 10
interface GigabitEthernet0/0/5
port link-type access
port default vlan 10
interface GigabitEthernet0/0/6
port link-type access
port default vlan 20
interface GigabitEthernet0/0/7
port link-type access
port default vlan 20
interface GigabitEthernet0/0/8
port link-type access
port default vlan 20
interface GigabitEthernet0/0/9
port link-type access
port default vlan 20
interface GigabitEthernet0/0/10
interface GigabitEthernet0/0/11
interface GigabitEthernet0/0/12
interface GigabitEthernet0/0/13
interface GigabitEthernet0/0/14
interface GigabitEthernet0/0/15
interface GigabitEthernet0/0/16
interface GigabitEthernet0/0/17
interface GigabitEthernet0/0/18
interface GigabitEthernet0/0/19
interface GigabitEthernet0/0/20
interface GigabitEthernet0/0/21
interface GigabitEthernet0/0/22
interface GigabitEthernet0/0/23
eth-trunk 1
interface GigabitEthernet0/0/24
eth-trunk 1
interface NULL0
user-interface con 0
user-interface vty 0 4
port-group 1
group-member GigabitEthernet0/0/2
group-member GigabitEthernet0/0/3
group-member GigabitEthernet0/0/4
group-member GigabitEthernet0/0/5
port-group 2
group-member GigabitEthernet0/0/6
group-member GigabitEthernet0/0/7
group-member GigabitEthernet0/0/8
group-member GigabitEthernet0/0/9
return
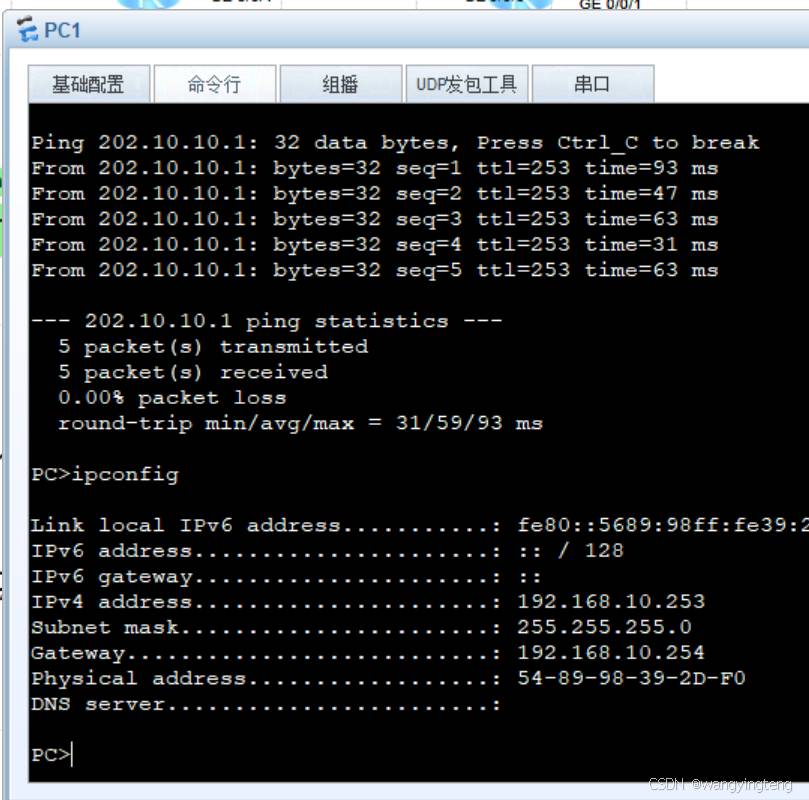
(8)分别在PC1、PC2上,设置DHCP动态获取IP地址,执行ipconfig命令,将输出结果分别截图粘贴至下面。
PC1:
版权说明:如非注明,本站文章均为 扬州驻场服务-网络设备调试-监控维修-南京泽同信息科技有限公司 原创,转载请注明出处和附带本文链接。
请在这里放置你的在线分享代码